NSA, GCHQ, and XKeyscore – missing nothing
 The Guardian in the last month has confirmed more or less everything I wrote back in June on Prism/Boundless intrusion. It’s true, tthe NSA/GCHQ are seeing everything.
The Guardian in the last month has confirmed more or less everything I wrote back in June on Prism/Boundless intrusion. It’s true, tthe NSA/GCHQ are seeing everything.
It’s not clear whether today’s revelations show that Snowden is still releasing information after his temporary asylum into Russia or whether it was done before he left the airport. Stopping the leaks was originally a condition of asylum, so it would be interesting and valuable if Russia had relaxed that requirement. And indeed if a condition of asylum was that they got access to everything. Either way, it’s clear that Snowden is doing us all a great service, and he deserves protection.
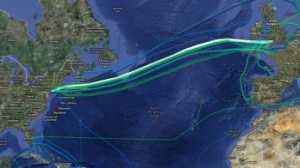 The story is unfolding in different sources at different times, so this is an attempt to put it all together (as of August 3rd). The latest revelation was actually revealed by the Süddeutsche Zeitung newspaper and ARD (the German equivalent of the BBC) and is shown in translation here. It identifies British Telecom, Verizon, Vodafone, the network operator Level 3, Global Crossing (now purchased by Level 3), Interoute and Viatel as the operators who give GCHQ unfettered access to their internet communications infrastructure. The same German team also revealed in June that BT monitors the TN-14 transatlantic cable, which carries almost all European traffic to the US and beyond.
The story is unfolding in different sources at different times, so this is an attempt to put it all together (as of August 3rd). The latest revelation was actually revealed by the Süddeutsche Zeitung newspaper and ARD (the German equivalent of the BBC) and is shown in translation here. It identifies British Telecom, Verizon, Vodafone, the network operator Level 3, Global Crossing (now purchased by Level 3), Interoute and Viatel as the operators who give GCHQ unfettered access to their internet communications infrastructure. The same German team also revealed in June that BT monitors the TN-14 transatlantic cable, which carries almost all European traffic to the US and beyond.
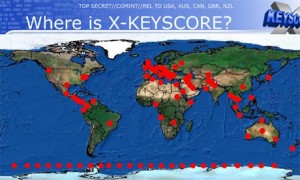 Many technically informed people are unconcerned by this on the basis that there is just too much data in these streams to analyse. However, huge strides have been made in analysis capability, along the lines of my earlier description – and the sophistication and power of the analysis tools surprises even me. The key program (the name of which I think was redacted in the earlier Snowden leaks and PowerPoint charts) is an NSA system called XKeyscore. The programme is fully described here, and the Powerpoint deck is shown here. You really should read these.
Many technically informed people are unconcerned by this on the basis that there is just too much data in these streams to analyse. However, huge strides have been made in analysis capability, along the lines of my earlier description – and the sophistication and power of the analysis tools surprises even me. The key program (the name of which I think was redacted in the earlier Snowden leaks and PowerPoint charts) is an NSA system called XKeyscore. The programme is fully described here, and the Powerpoint deck is shown here. You really should read these.
If you don’t have time – here’s a potted overview. As I noted in June, NSA/GCHQ have the power to identify all data, down to email content and Facebook posts from the inline stream – they do not need access to Gmail or Facebook do this. In 2009 they could store everything for 3 days, and metadata (email addresses, phone numbers, people contacted etc) for 30 days.
 Now it is true that no human(s) could analyse all this in real time. As a result, much of the tracking and analysis process it is automated. What triggers deeper analysis? Chart 15 gives a clue: ‘anomalous events’: specifically, ‘someone whose language is out of place for the region they are in, someone who is using encryption, or someone who is searching the web for suspicious stuff’. Also using VPN services (to avoid your local ISP tracking you), or password protecting a MS Word file will trigger suspicion. Sound like anything you do? Note in particular that any attempt to avoid snooping by using VPNs, or encryption will automatically get you targeted. And don’t be under any illusion that NSA/GCHQ cannot crack your puny encryption.
Now it is true that no human(s) could analyse all this in real time. As a result, much of the tracking and analysis process it is automated. What triggers deeper analysis? Chart 15 gives a clue: ‘anomalous events’: specifically, ‘someone whose language is out of place for the region they are in, someone who is using encryption, or someone who is searching the web for suspicious stuff’. Also using VPN services (to avoid your local ISP tracking you), or password protecting a MS Word file will trigger suspicion. Sound like anything you do? Note in particular that any attempt to avoid snooping by using VPNs, or encryption will automatically get you targeted. And don’t be under any illusion that NSA/GCHQ cannot crack your puny encryption.
Note also that the information dates from 2009, 4 years ago. Processor technology in particular has moved on hugely since then and the retention and analysis capabilities will be vastly superior now. In slide 32 ‘Future’, ‘higher speeds yet again’ via specialized ‘algorthimic and cell processors’ are mentioned. The cell processor is the GPU-like technology developed by IBM for the Sony playstation by the way. Also coming in 2009 was VOIP (Skype), and EXIF (the information tags embedded into your photographs by the camera you use – including GPS location data). So there is nothing you do that isn’t being seen, including by the way all Google searches and Google maps sessions. Looking at somewhere suspicious on the map? You’ve got a friend watching you.
Another revelation from the Guardian this week was that large amounts of the UK end of this work (particularly European and Transatlantic tapping of all data lines) is funded by the NSA. Why would the Americans do this? Firstly because the UK has unique access to global communications systems as they cross to the US. And second, the US has (in principle) tough laws regarding privacy in the US, which they can essentially ignore when operating by proxy in the UK. And of course the UK also ignores all European privacy laws too, up to and including tapping into European data lines.
 Think about that for a minute. The US is a country which has for 11 years illegally rendered foreign nationals and tortured them, has over it’s history illegally conducted internal wars other countries, and has a long list of other internal injustices which we are all familiar with. And the UK has positioned itself to the lax side of that? This I think started with the odious Jack Straw and the rest of the New Labour home secretaries intoxicated with Iraq and their own power. And it has led us down a very slippery slope. I vastly prefer the European approach to privacy and snooping. The Germans had their own Stasi, and removed it. We still have ours and it continues on growing and further invading our lives while we enjoy the summer heat.
Think about that for a minute. The US is a country which has for 11 years illegally rendered foreign nationals and tortured them, has over it’s history illegally conducted internal wars other countries, and has a long list of other internal injustices which we are all familiar with. And the UK has positioned itself to the lax side of that? This I think started with the odious Jack Straw and the rest of the New Labour home secretaries intoxicated with Iraq and their own power. And it has led us down a very slippery slope. I vastly prefer the European approach to privacy and snooping. The Germans had their own Stasi, and removed it. We still have ours and it continues on growing and further invading our lives while we enjoy the summer heat.


